Cloud-Dateisicherheitssoftware Ressourcen
Artikel, Diskussionen, und Berichte, um Ihr Wissen über Cloud-Dateisicherheitssoftware zu erweitern
Ressourcenseiten sind darauf ausgelegt, Ihnen einen Querschnitt der Informationen zu bieten, die wir zu spezifischen Kategorien haben. Sie finden Artikel von unseren Experten, Diskussionen von Benutzern wie Ihnen, und Berichte aus Branchendaten.
Cloud-Dateisicherheitssoftware Artikel
How To Tell if Your Phone Is Hacked and What To Do
If you’ve noticed your phone acting strangely–apps crashing, battery draining faster than usual, or unfamiliar pop-ups–it’s natural to wonder "is my phone hacked?"
von Holly Landis
Was ist Cloud-Sicherheit? Die Grundlagen der Cloud verstehen
Wenn ein Unternehmen beschließt, seine Daten in die Cloud zu verlagern, stellt sich immer die grundlegende Frage der Sicherheit.
von Mara Calvello
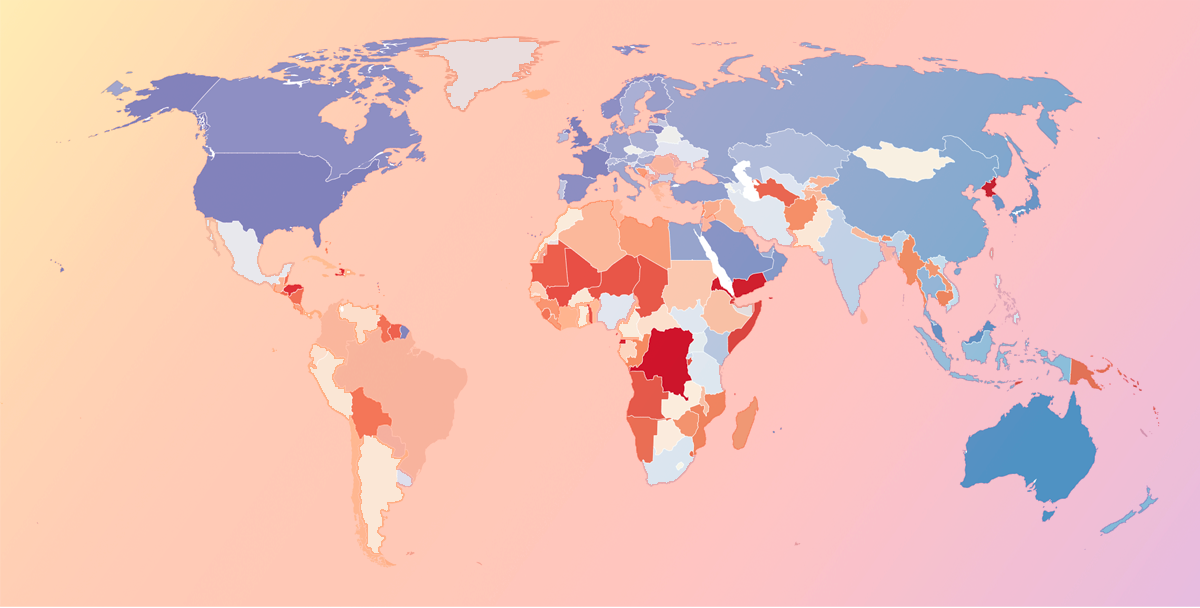
National Cybersecurity and Popular Products Across the World
In a digital age, data security is a top priority, but it can be difficult to know who exactly is responsible for securing sensitive information. While companies may feel they have sufficiently secured their own data, those that utilize SaaS vendors in their business put their sensitive information and business data in the hands of these vendors, who store it in the cloud or on-premises at their location.
There are a number of security considerations and variables a business should keep in mind, especially related to cloud security. But it's helpful to remember one simple question when considering vendors or evaluating current protection efforts: Does the country housing my data care about security?
Countries that do have taken action to protect personal and business data stored in their country or region. Other efforts to protect personal information include enforcing security standards, developing national cybersecurity strategies, and providing public awareness campaigns, among others. Countries that received lower scores have done less to ensure businesses are protecting data and require less transparency between data collectors and individuals.
In a globalized world, servers could be housed in any number of countries other than the one your business or a software vendor operates in. Still, it should be considered a potential red flag if vendors operate out of extremely vulnerable geographical regions.
Every year, the International Telecommunication Union (ITU) releases the results of a worldwide security survey titled the United Nations Global Cybersecurity Index (CGI). The index provides an overall security rating based on a number of factors related to legislative, organizational, technical, capacity building, and international cooperation.
von Aaron Walker
Cloud-Dateisicherheitssoftware Diskussionen
0
Frage zu: Microsoft Defender for Cloud Apps
Wofür wird Microsoft Defender for Cloud Apps verwendet?Wofür wird Microsoft Defender for Cloud Apps verwendet?
Auf hoher Ebene handelt es sich um eine CASB-Lösung zur Verwaltung von Schatten-IT, aber sie verfügt über viele Funktionen, einschließlich einiger DLP- und Haltungsmanagement.
0
Frage zu: SpinOne
Wofür wird SpinOne verwendet?Wofür wird SpinOne verwendet?
SpinOne ist eine All-in-One-SaaS-Sicherheitsplattform, die SaaS-Daten vor Datenlecks und Datenverlust schützt, indem sie Organisationen hilft, Sicherheits- und Compliance-Risiken zu reduzieren, Zeit für SecOps-Teams zu sparen, Ausfallzeiten und Wiederherstellungskosten bei Ransomware-Angriffen zu senken und die Compliance zu verbessern.
Cloud-Dateisicherheitssoftware Berichte
Momentum Grid® Report for Cloud File Security
Summer 2025
G2-Bericht: Momentum Grid® Report
Mid-Market Grid® Report for Cloud File Security
Summer 2025
G2-Bericht: Grid® Report
Small-Business Grid® Report for Cloud File Security
Summer 2025
G2-Bericht: Grid® Report
Grid® Report for Cloud File Security
Summer 2025
G2-Bericht: Grid® Report
Small-Business Grid® Report for Cloud File Security
Spring 2025
G2-Bericht: Grid® Report
Grid® Report for Cloud File Security
Spring 2025
G2-Bericht: Grid® Report
Momentum Grid® Report for Cloud File Security
Spring 2025
G2-Bericht: Momentum Grid® Report
Mid-Market Grid® Report for Cloud File Security
Spring 2025
G2-Bericht: Grid® Report
Enterprise Grid® Report for Cloud File Security
Winter 2025
G2-Bericht: Grid® Report
Mid-Market Grid® Report for Cloud File Security
Winter 2025
G2-Bericht: Grid® Report