Virtual desktop infrastructure (VDI) offers a world of business benefits in the shape of productivity, performance, and functionality. However, there is a common concern among VDI users: security.
While the ability to connect to a virtual version of your desktop from anywhere in the world is incredibly convenient, users can’t help but think about the security risks associated with that high level of accessibility.
As users become acquainted with VDI, they might find themselves considering the following setbacks:
- What are the most significant threats to my data when using a VDI?
- What if my desktop is accessed by an unauthenticated user?
- How can I be sure that all of my information that I access using a VDI is safe?
To properly and safely equip your workforce with the convenience of connecting to your company’s central servers from any device they please, you must first address security by understanding the threats at hand, how to combat them, and best practices for avoiding them in the future.
VDI security threats
A key feature that attracts VDI users is the fact that no data is stored on their endpoint devices. Instead, the information is stored on the organization's central server and simply accessed on those endpoint devices.
While this aspect of VDI comes in handy when devices are stolen, it’s a different story if they are compromised by a threat.
Before you get started implementing your VDI, it’s best to understand the present security threats that you might encounter while going about your business.
There are two pressing security risks that become relevant once your organization has started using its VDI: remote access trojans and the man in the middle.
Remote access trojans
Named for the sneaky military strategy implemented by the Greeks to attack the city of Troy, a computer trojan is a type of malicious software that disguises itself as a safe application to install on your computer that actually causes damage to the device.
A remote access trojan, accurately represented by its nickname RAT, is a program that gains unauthorized access to a personal computer. RATs act in similar ways to keyloggers, which record keyboard activity to learn usernames, passwords, and other personal information.
Once RATs have gained access to the victim's personal computer, they can monitor the behavior of the user remotely, change computer settings, and browse files within the desktop, all with the intention of harming the associated organization.
Essentially, a RAT has the capabilities of any other end-user of your VDI. They’re just unauthorized.
If you’ve found RAT programs in your device’s system, it’s safe to say the personal information held on that device has been compromised. Should this happen to one of your VDI end users, make it clear that they should immediately notify the administrator and update all of their usernames and passwords from a clean computer.
Man in the middle
In the dreaded man in the middle (MITM) attack, the unauthorized party attacks an individual’s device and either relays or alters (or both) communication between two parties. However, the intended parties are completely unaware that their communication is being intercepted by the attacker.
This style of attack is used to eavesdrop, gather private information, or change the direction of a conversation to work in their favor.
For these MITM attacks to work for the intruder, they must convince both parties involved in the communication that they are in fact the other party the message was intended to reach.
Similar to RAT attacks, if a device has been infiltrated by a MITM, it’s safe to say that all information that was passed along via communication on that device has been compromised.
Want to learn more about Virtual Desktop Infrastructure (VDI) Software? Explore Virtual Desktop Infrastructure (VDI) products.
VDI security best practices
Your data is precious, and the threat of it being compromised by a hacker has never been more present.
While there are certain security risks associated with implementing a VDI within your organization, there are also some best practices you can implement that will help you avoid these mishaps.
Take a connected approach
The purpose of using VDI software within your organization is to be able to access your remote desktops from a variety of end-user devices. While the convenience of VDI is hard to beat, it’s difficult to manage every single device being used to access a virtual desktop instance.
This is where security threats become an issue. With so many devices connecting to your central server, it can be hard to keep track of them all. Not to mention that the more devices you have that regularly connect to your VDI, the more attackable points of vulnerability you have.
Take a cohesive approach as you go about protecting your VDI endpoints from security threats. Every device in use must be featured in your security plan. By strengthening the weak links that exist in your device network, you can ensure that your data will be kept safe.
Choose a platform carefully
As you implement your VDI and allow your intended end-users to access their data and virtual desktops, you’re placing a lot of trust in the security that your chosen software offers.
Most VDI platforms already have built-in layers of security within the designated network, but, again, as those devices keep adding up, security becomes more of a concern.
When choosing a VDI platform for your organization, pay special attention to the security features and how well it runs across multiple operating systems of the endpoint devices in use. Because VDI allows for people within your organization to use their own devices to access their virtual desktops, you need to make sure that the security complies with MacOS, Windows, and other operating systems.
To be even more careful, you can also implement an extra layer of security with endpoint management software, which keeps track of the devices being used within a system to ensure their software is secure and up to date.
On top of that, endpoint management tools make sure that no unauthorized devices are connected to your central server.
Encrypt everything
While information is only accessible on these endpoint devices, not stored on it, those devices still give users access to it, whether they’re authorized or not. In the face of a MITM attack, where hackers can intercept any information being sent or received, you need to be sure to encrypt absolutely everything.
Encryption is a method used to hide information’s true meaning to unauthorized parties. This security measure uses algorithms to convert the original information, also known as plaintext, into ciphertext, which is only decipherable with a key. That ciphertext is transmitted, and the recipient can then decode that message with the key.
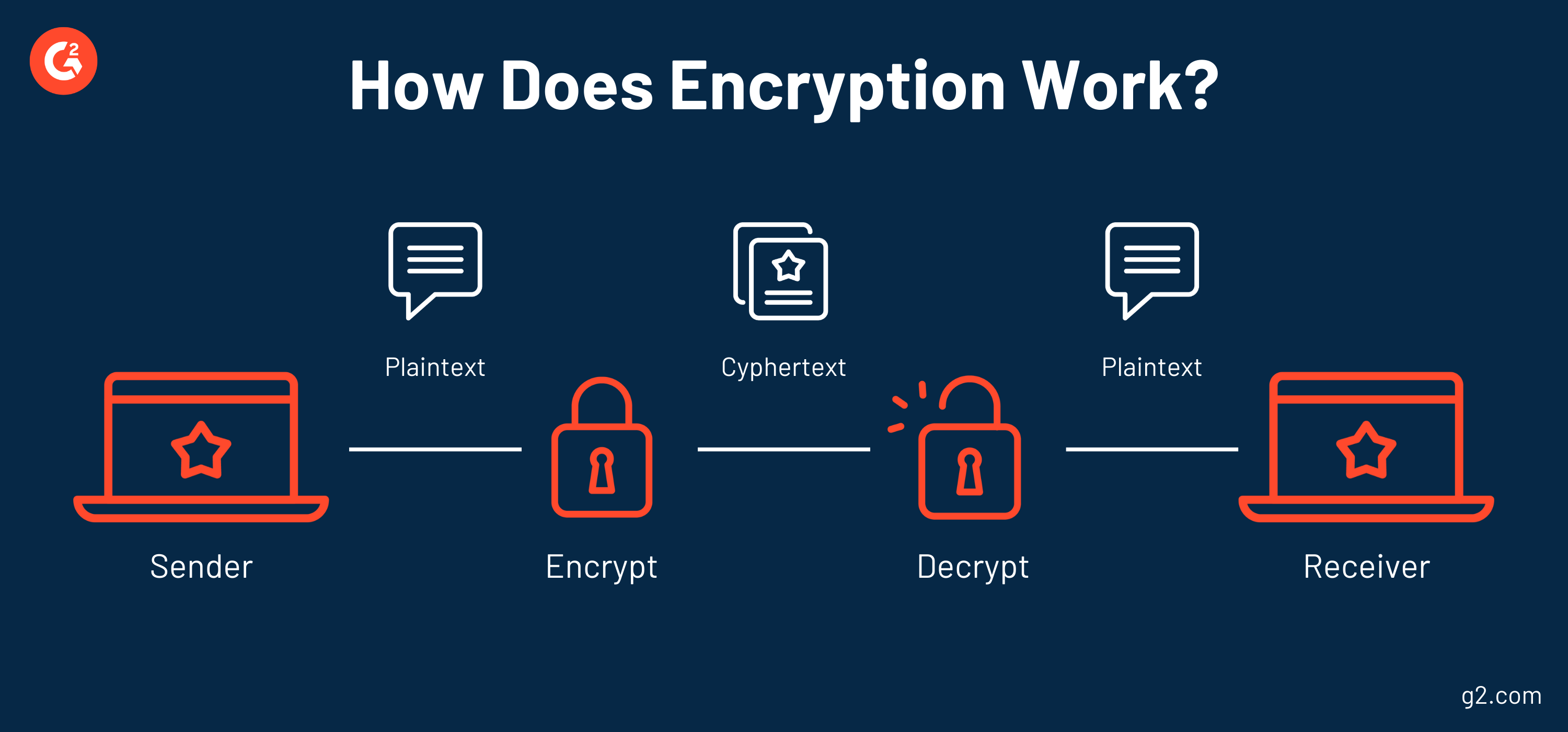
Encryption doesn’t deny access to unauthorized users but instead makes it so they can’t understand the information they’ve gained access to. As you store sensitive information on the virtual desktops that connect to your central server, use encryption to make sure it isn’t stolen by an undesirable third party.
Use thin clients
While RATs and MITM propose threats to your VDI’s security, sometimes even the authenticated users connecting to your central server can worsen the situation if they aren’t careful.
Users installing new applications or changing computer settings might be putting the security of your organization at risk without even realizing it. Again, the more users that connect to the central server of your virtual desktop infrastructure, the more points of vulnerability you present to hackers.
While virtual desktop infrastructure allows administrators to control the apps that users install on their endpoint devices, another best practice is using thin clients to optimize your VDI’s security.
A thin client is a computer that has been developed to establish a remote connection with a server. The server does all of the work, like launching applications or storing data.
Essentially, a thin client is a computer that can’t function without being connected to a central server. The key factor of thin clients is that while they allow users to connect to your VDI’s central server, they do not allow them to make changes to the applications, meaning they can’t install malware.
Employ antivirus software
Virtual desktops make it easier for administrators to slow the spread of malware and viruses on endpoint devices, but they do not remove the initial threat altogether. While many VDI software providers offer top-notch security built into their solution, it’s never a bad idea to pair your VDI with antivirus software.
Hackers are tricky these days, and they’re only getting smarter. Certain links in strange-ish emails might seem innocent enough, but once they’ve been clicked, they can present a larger threat to your entire organization.
Antivirus software actively protects your devices by preventing and detecting the presence of any malicious software that might’ve been accidentally installed. These tools not only include detection features that will identify potential malware or viruses, but also some form of firewall, which will stop the infiltrators in the first place.
Yes, adding another software tool to your tech stack might make you roll your eyes and ideate excuses for not investing in it. However, when it comes to the security of your organization’s private information, it’s best to play it safe.
Be wary of BYOD
There are plenty of organizations that allow users to connect to their virtual desktops from their own personal and unmanaged devices, also known as a bring your own device (BYOD) policy.
While this can be an effective method for saving on hardware costs, it can present trouble if those personal devices are compromised.
If that's the case, an attacker can gain access to your organization's VDI through that endpoint device. From there, they can impersonate the user, access your sensitive information, and alter the configuration of that desktop instance if they wish. And the worst part, this doesn't even take advanced hacking skills - with the right tools, anyone can do it.
If your organization has a BYOD policy, here are some extra precautions you can take to make sure only authenticated users are connecting to your organization's VDI:
- Use password protected access controls and extra precautions like single sign-on software
- Control wireless network and server connectivity by prompting users before they connect to a network to make sure it's safe
- Govern the applications users have access to
- Make sure to keep your operating systems, software, and applications up to date so new security precautions can be applied
- Backup your data
Get input from IT
As always, with any new software move or implementation, let your IT department be your guiding light.
IT isn’t just there to make sure everyone’s computer monitor is working properly anymore. They are the technology experts within your organization - they control what people can and cannot do online, manage infrastructure, and find ways to make your organization’s technology more secure and efficient.
Your IT department should be a key stakeholder in your VDI security plans. Not only do they have extensive knowledge in the technical groundwork of your organization, but they can also offer sound advice as you tackle these issues.
Secure your systems
Security should be at the forefront of any software strategy, especially one that has such a significant impact on your entire organization like VDI.
Threats to your organization’s security and software systems are always going to be present, but prioritizing the best practices above will allow you to operate a VDI without worrying about protection.
Wondering what else can help keep your organization’s data and network safe? We've got you covered. Checkout our comprehensive guide on VPNs.

Mary Clare Novak
Mary Clare Novak is a former Content Marketing Specialist at G2 based in Burlington, Vermont, where she is explored topics related to sales and customer relationship management. In her free time, you can find her doing a crossword puzzle, listening to cover bands, or eating fish tacos. (she/her/hers)
